Hybrid Azure Active Directory
Hybrid Azure Active Directory is a mode that allows you to manage and register devices both via traditional on-premises active directory tools and with azure active directory.
In this article I will try to give you a brief overview of what an architecture of Hybrid Azure Active Directory. Nowadays everybody wants to more about hybrid azure active directory so, Let's try to cover deep drive on it.
Why everyone wants to manage these apps whether the third-party apps Microsoft apps on-premises apps from a centralized repository Azure active directory. One of the main reasons why is so you can have single sign-on to all of those applications been on-premises applications.`
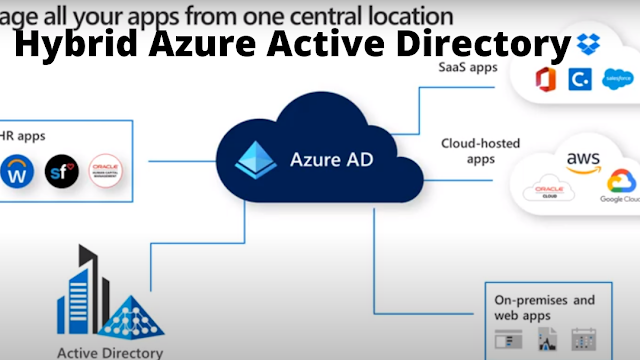
Once those apps are integrated you' all be able o then protect and govern access to those apps and here you could see some of those. Enable seamless user experience with single sign-on.
There are some different methods to do that and then use when my absolute favorite features and that's conditional access and here you could see and if-then statement for every time a user goes to authenticate against one of those apps.
There are really three different integration scenarios for azure active directory.
Hybrid Topologies
Cloud Identity: is an identity as a service and enterprise mobility management product. it offers the identity service and also endpoint administration that is available in G Suite as a stand-alone product.Synchronized identity: We can manage the user identity in an on-premise server and synchronize the accounts. It's and single identity enabling the same or single sign-on experience with password hash sync or pass-through authentication.
Featured identity: It's and single featured identity enabling single sign-on experience and on-premises multi-factor authentication options.
I will tell you from my personal experience that what you're business outcome depends upon and what you trying to do but for most organization password hash sync and seamless SSO is going to work just fine other organization. They may want to do Pass-through authentication while some who have very specific requirements.
Password Hash Sync:
I am a fan of Password hash sync because it's really simple. We're synchronizing a hash of the users password from windows Server Active Directory up to Azure. Active Directory and this gives you a lot of capabilities it gives you single sign-on to your third-party apps and also Microsoft Apps and even on-premises Web App. It gives you a report to see users credentials that are up for sale on the dark web. It prices you access to things like credentials access. There is no requirement of any agent. It really works all right the net one is passed throughout.
Pass-through authentication:
Pass-through authentication can provide you better user experience and also provides the other things like smart lockout and conditions access and some other items. The biggest difference is that when a customer wants to use on-premises based smart card they're an on--premises-based MFA solution then we will use ad FS in out of federated topology.
Why Choose Managed over Federated?
Less on-premises infrastructure:
1.PHS: AAD connect server facilities this process
2.PTA: Agents deployed on existing servers (physical/virtual)
3.Seamless SSO- Provided via existing AD infrastructure (Computer Account)
Same or better end-user sign in experience
1.No smart link requirements
2.Modern Authentication and KMSI for continued SSO.
3. Windows 10 Hybrid AADJ gives the best SSO experience
Smart Lockout
1.Gain instant Protection for identities
2.On by default and smarter than AD FS extranet lockout
3. Customizable Lockout bd actor after X failed password attempts







